ProcessBolt ThreatScape
Attack Surface Management Platform protects against gaps in your company’s and your vendors’ digital ecosystem by identifying and monitoring internet facing assets.
ThreatScape Attack Surface Management Platform
Risks are monitored, threats are detected, alerts are issued immediately, and actionable intelligence is provided to mitigate threats in real-time.
ProcessBolt ThreatScape Provides Real-Time Threat Intelligence
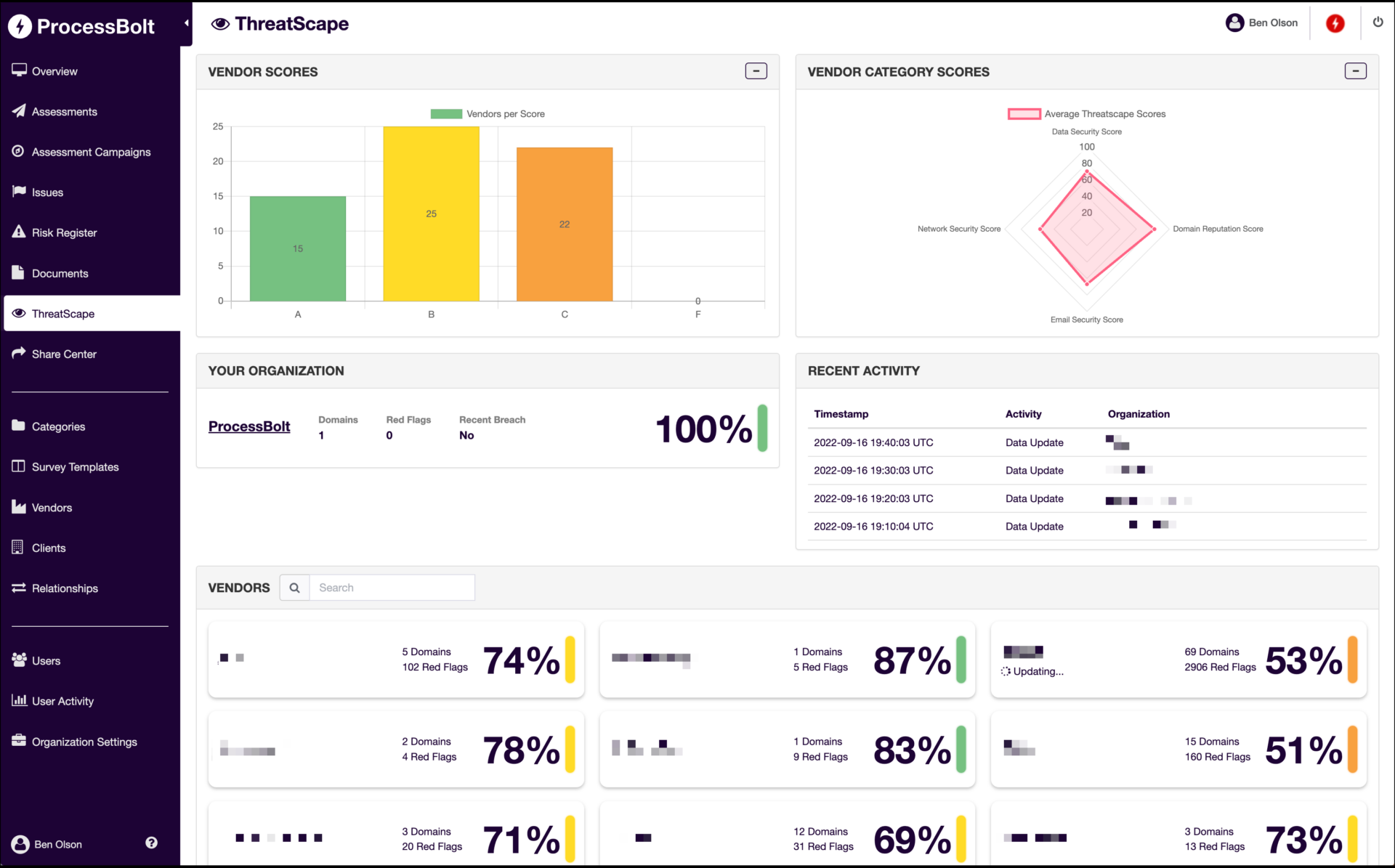
ProcessBolt ThreatScape is an attack surface monitoring tool that enables you to continuously monitor your vendors and identify adverse changes in their security posture.
ProcessBolt’s ThreatScape actively correlates attack surface data with assessment responses, ensuring the alignment and consistency between the two.
With ThreatScape, you can detect adverse changes in your vendors’ security posture continuously, and leverage attack surface data to verify assessment responses.
Data Collection
ThreatScape’s proprietary sourcing algorithm gives it the unique ability to provide the most accurate and real-time attack surface intelligence possible.
ThreatScape sources its own data instead of relying on purchased, often stale batched data. Identify risks that may not be uncovered in the vendor risk assessment process or risks that surface in between assessments.
Rating
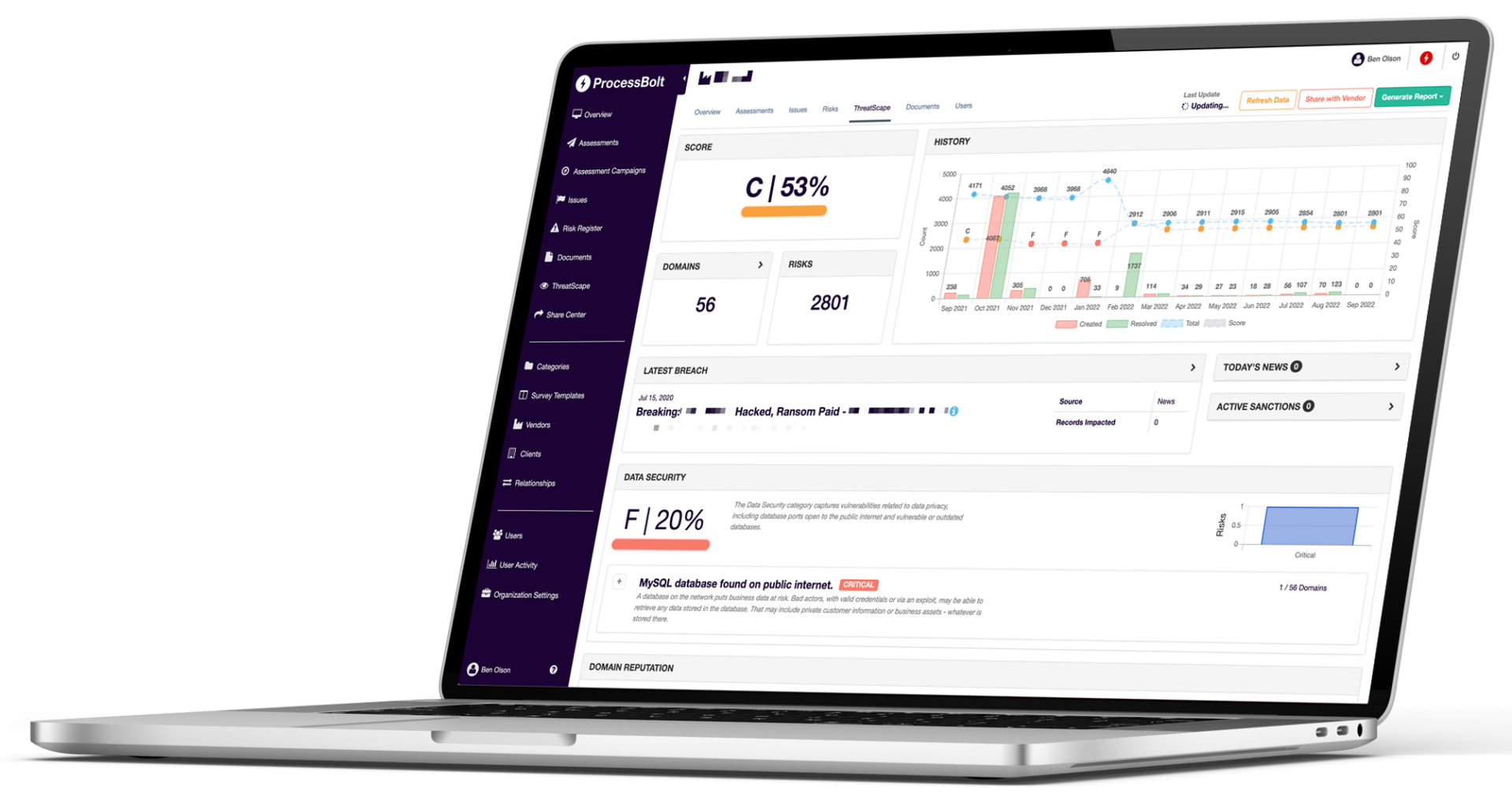
ThreatScape’s proprietary scoring algorithm looks at billions of data points to calculate a vendor score across 4 different domains – data security, domain reputation, e-mail security, and network security.
Customer definable scoring methodology helps clients define their business context with their vendors to get an accurate picture of their security risk exposure.
Actionable Intelligence
ThreatScape provides actionable insights for risks that are identified, enabling organizations to share these findings at no cost, ensuring timely remediation of issues.
Effortless Reporting
Easy-to-understand dashboards and reports provide you with complete visibility into your own, and your vendor network’s attack surfaces.
How ThreatScape Works
Features & Benefits
Real-Time Attack Surface Data
We source all of our data internally and do not rely on batch data, which is often stale
Real-Time Alerts
ThreatScape notifies you of any adverse changes in an organization’s security posture, ensuring that these gaps in security are immediately addressed before it is too late
Fully-Integrated
ThreatScape correlates attack surface data with assessment responses, ensuring the alignment and consistency between the two
Facilitates Timely Remediation
We provide actionable intelligence and do not charge vendors to receive access to their ThreatScape findings, making sure they have access to all relevant information so they can remediate risks
Gain Insight and Automate Alerts to Reduce Risk
Get your Free ThreatScape Report Today!
ProcessBolt’s ThreatScape can help you protect against gaps in your company’s and your vendors’ digital ecosystem by identifying and monitoring internet-facing assets in real-time. Get your free ThreatScape report today.
You May Also Like…
Building a Foundation for Strong Third-Party Risk Management
Discover how to build an effective third-party risk management program with vendor tiering, regular assessments, continuous monitoring, and modern automation tools.
How to Identify and Mitigate Third-Party Risk
Learn how to mitigate third-party risk with proactive strategies like access control, vendor tiering, and continuous monitoring to protect your organization.
Addressing the Rising Cybersecurity Threats in Manufacturing
Manufacturing cybersecurity threats are rising fast. Discover how to secure your supply chain through monitoring, employee training, and third-party risk management.