ProcessBolt AI
ProcessBolt AI is transforming the vendor risk assessment process, leveraging AI and attack surface data to complete risk assessments
Best in Class Vendor Risk Management Solution
ProcessBolt AI is a fully integrated AI-driven platform that extracts intelligence directly from vendor policy documents to populate security assessments and correlates that data with the vendor’s attack surface intelligence, reducing the assessment timelines from weeks to minutes.
ProcessBolt AI Elevates the Vendor Risk Management Lifecycle
ProcessBolt AI offers an automated vendor risk assessment, and real-time threat monitoring platform to enable organizations to efficiently manage third-party risk. The integrated platform automates time-consuming and manual processes, and eliminates the need for disparate software solutions, saving users up to 80% of the time it takes to manage third-party security risks.
The fully integrated AI-driven platform leverages attack surface management data, vendor evidentiary documentation, and assessment data to complete vendor risk assessments, removing an enormous amount of friction that plagues the current vendor risk management process.

Pre-Assessment
Vendor Intake/Onboarding
Develop workflows to onboard new vendors, giving procurement and risk management teams a holistic view of their vendor network and supplier risk profiles within the ProcessBolt platform.
Build Assessment
Build custom assessments or leverage our library’s extensive industry templates (SIG, ISO, NIST, etc.).
Categorize Vendors Based on Risk Levels
Our workflow-driven platform tiers vendors based on levels of risk, providing organizations with visibility into the level of diligence required for each of your third parties.

Assessment
Collect Vendor Documentation
Instead of sending out long and detailed risk assessments to begin the process, vendors put all the requested policy documents and audits into the ProcessBolt platform.
Populate Assessment Responses
ProcessBolt AI then reviews all documentation using the latest generative AI technology and answers assessment questions, adding citations from the documentation to each question so that the vendor and enterprise can verify assessment responses.
Correlate Attack Surface Data to Assessment Responses
ThreatScape simultaneously looks at all internet-facing attack surfaces of the vendor and correlates this data to the assessment responses, verifying that the assessment responses are consistent with attack surface data.
Vendors Complete the Assessment
ProcessBolt shares the assessment answers with the vendor. All the vendor has to do is review and confirm the veracity of the AI-generated answers and answer any questions that could not be answered by company documentation or attack surface data.
Organization Reviews and Verifies Assessment
The fully completed assessment is returned to the organization and they can quickly verify the accuracy of the answers by leveraging citations from policy documents and attack surface data.

Post Assessment
Issue Management & Risk Remediation
ProcessBolt automatically creates issues based on assessment responses, making it easy for organizations to document and record issues, and ensure timely remediation.
Continuous Monitoring
Proactively monitor vendors in real-time to identify adverse changes in their security posture in between assessments.
Analytics
Leverage custom dashboards and reporting to provide various stakeholders with key insights related to vendor risk.
Features & Benefits
Assessment Verification
ProcessBolt AI reads all policy documentation and adds citations to each assessment response, ensuring instant verification of responses
Fully-Integrated
Attack surface data correlated to assessment responses, ensuring the alignment and consistency between the two
Configurable
The platform makes it easy to configure complex workflows and scoping to fit the needs of an organization
Adaptable
Framework agnostic platform enables organizations to build a custom assessment or leverage our robust library of templated questionnaires such as NIST, ISO, SIG, ESG, and HIPAA
Intuitive and Easy to Operate
The platform enables a single person in an organization to manage the entire vendor risk management process
Comprehensive
Easy to understand dashboards and reports provide you complete visibility into your own, and your vendor network’s security posture
Eliminate Vendor Fatigue
Assessment responses populated from corporate documentation, reducing vendor workload
Time-Saving:
Reduce the assessment timelines from weeks to minutes
No Hidden Fees
One price – no hidden services fees
ProcessBolt AI is Disrupting the Vendor Risk Management Process!
Instead of sending out long and detailed risk assessments to begin the process, vendors put all the requested policy documents and audits into the ProcessBolt platform. ProcessBolt AI then reviews all documentation using the latest generative AI technology and answers assessment questions, adding citations from the documentation to each question so that the vendor and enterprise can verify assessment responses. At the same time, ProcessBolt’s ThreatScape module is looking at all internet-facing attack surfaces of the vendor and correlating this data to the assessment responses, verifying that the assessment responses are consistent with attack surface data.
Why You Need ProcessBolt AI Vendor Risk Management!
%
SECURITY BREACHES ARE RELATED TO SUPPLY CHAIN
AVERAGE COST OF A SECURITY BREACH
%
EXPECTED INCREASE IN SUPPLY CHAIN RELATED INTRUSIONS
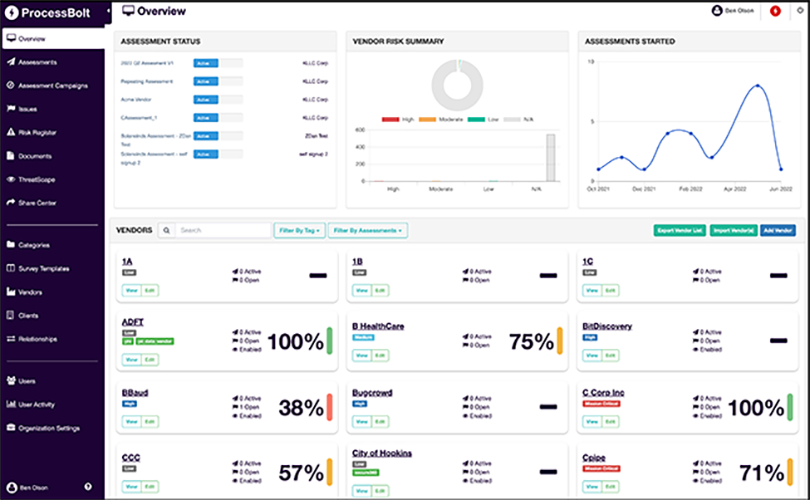
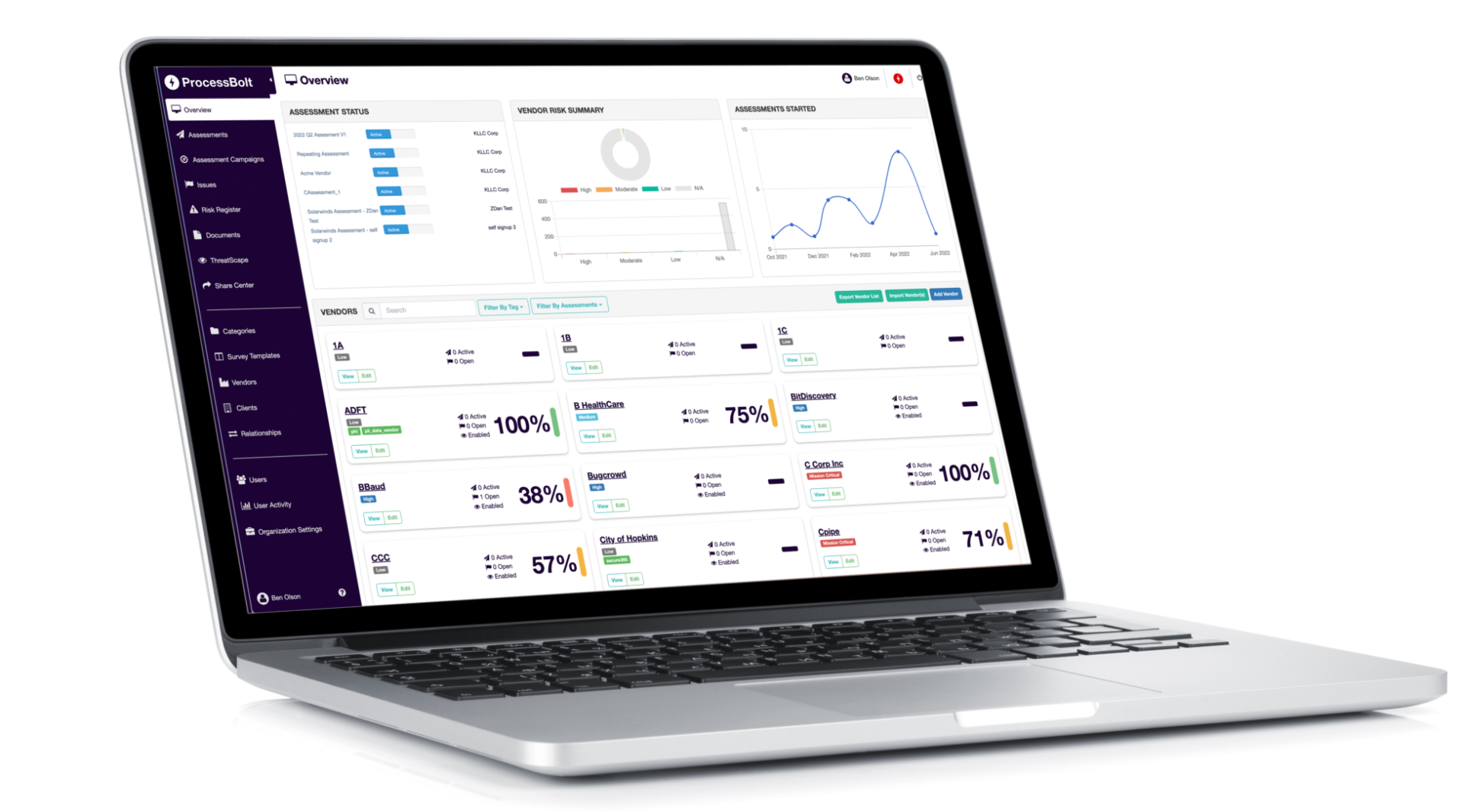
See How Easy ProcessBolt AI Works!
Sign up and receive a personalized demo that shows how ProcessBolt AI is transforming the risk assessment process.
Trusted by Top Brands

You May Also Like…
How Tariffs Impact Manufacturing Security
Tariffs reshape manufacturing security by driving supplier shifts, workforce cuts, and documentation risk. Learn how to adapt your cybersecurity and TPRM strategies.
How Manual Vendor Assessments Are Killing Your Team’s Productivity
Manual vendor risk assessments drain time, create security gaps, and stall strategic work. Learn how automation with ProcessBolt helps teams move faster.
Building a Foundation for Strong Third-Party Risk Management
Discover how to build an effective third-party risk management program with vendor tiering, regular assessments, continuous monitoring, and modern automation tools.