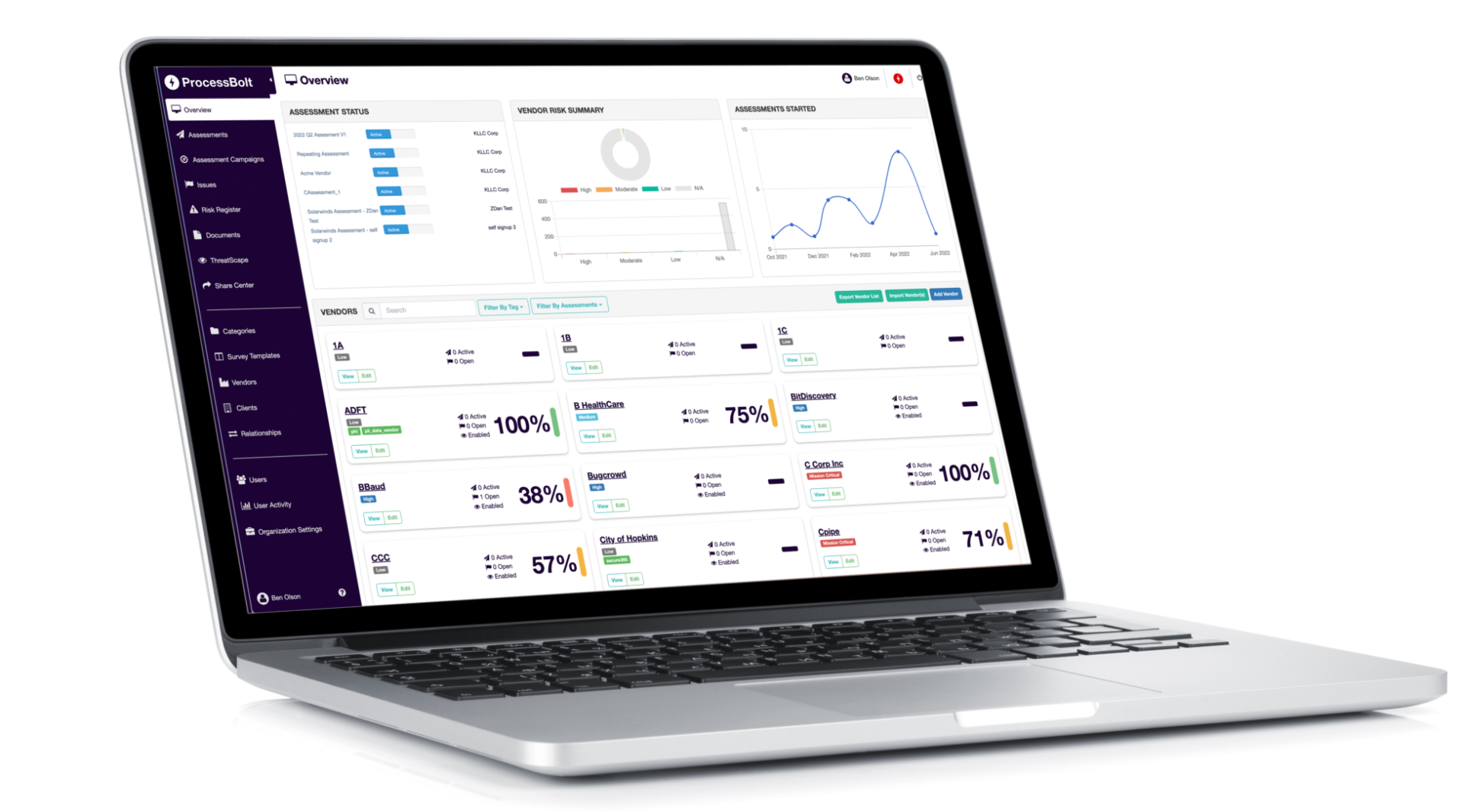
Third-Party Continuous Monitoring
ProcessBolt AI – The Future of Third-Party Continuous Monitoring
Ready to effortlessly take control of your third-party risk and compliance? ProcessBolt is transforming the vendor risk management process by integrating attack surface management with AI-driven assessment automation. The fully-integrated, AI-driven platform leverages attack surface management data, vendor evidentiary documentation, and assessment data to complete vendor risk assessments, removing an enormous amount of friction that plagues the current vendor risk management process. The integrated platform automates time-consuming and manual processes, and eliminates the need for disparate software solutions, saving users up to 80% of the time it takes to manage third-party security risks.See How Easy ProcessBolt Works!
Sign up and receive a personalized demo that shows how ProcessBolt AI is transforming vendor risk management.
Best in Class Vendor Risk Management Solution






What Makes ProcessBolt Different?
Fully Integrated Platform
Multi-Layer Trust & Verification
Extract intelligence from corporate documentation and attack surface data for instant verification of assessment responses
Real-Time Threat Intelligence
Identify adverse changes in vendor security posture in real-time
Rapid Onboarding
Start using the platform in a matter of Hours/Days
End-to-End Platform
Managed Services (optional)
ProcessBolt AI All-In-One Integrated Platform

Collect and Verify Vendor Documentation
Instead of sending out long and detailed risk assessments to begin the process, vendors put all the requested policy documents and audits into the ProcessBolt platform. ProcessBolt AI then reviews all documentation using the latest generative AI technology and populates responses to assessment questions, adding citations from the documentation to each question so that the vendor and enterprise can verify assessment responses.

Simultaneously Correlate Attack Surface Data
ProcessBolt’s ThreatScape actively correlates attack surface data with assessment responses, ensuring the alignment and consistency between the two. By simultaneously analyzing the vendor’s internet-facing attack surfaces and assessment responses, ThreatScape validates the accuracy of the assessment by verifying its correspondence with real-world attack surface data.

Seamless Assessment Review
ProcessBolt then shares the assessment answers with the vendor. All the vendor has to do is review and confirm the veracity of the AI-generated responses and answer any questions that could not be answered by company documentation or attack surface data. The fully completed assessment is returned to the organization and they can quickly verify the accuracy of the answers by leveraging citations from policy documents and attack surface data.
What Users Say
"Customer Experience is Great!"
The Processbolt team has been incredibly receptive to feedback and requests for help. Processbolt has been essential to us being able to track and be able to complete security assessments."Customer Experience is Great!"
The Processbolt team has been incredibly receptive to feedback and requests for help. Processbolt has been essential to us being able to track and be able to complete security assessments."Best Vendor Management Tool!"
ProcessBolt was very fast for our team to implement and start using. They also have an unlimited user model, which works in our favor, and the platform is straightforward to use."Best Vendor Management Tool!"
ProcessBolt was very fast for our team to implement and start using. They also have an unlimited user model, which works in our favor, and the platform is straightforward to use."Win with ProcessBolt"
ProcessBolt makes it easy to automate our vendor management process. The team is really helpful and truly care about us getting value out of the system, which we do."Win with ProcessBolt"
ProcessBolt makes it easy to automate our vendor management process. The team is really helpful and truly care about us getting value out of the system, which we do."GREAT ASSESSMENT PLATFORM"
ProcessBolt is an extremely easy-to-use and flexible assessment platform. The tool is agnostic to any one methodology. It can be customized to your company’s specific rule sets to measure vendor’s risk or leverage one of ProcessBolt’s templates. Their support team is super helpful if you want to get more detailed, and the team is always willing to help walk you through something."GREAT ASSESSMENT PLATFORM"
ProcessBolt is an extremely easy-to-use and flexible assessment platform. The tool is agnostic to any one methodology. It can be customized to your company’s specific rule sets to measure vendor’s risk or leverage one of ProcessBolt’s templates. Their support team is super helpful if you want to get more detailed, and the team is always willing to help walk you through something.Trusted by Top Brands