While the healthcare industry continues to innovate in areas like diagnostics, treatment delivery, and patient engagement, much of the infrastructure that powers hospital operations remains stuck in the past.
It’s difficult to overstate the consequences of using these outdated systems — breaches made possible by legacy systems have disrupted care, delayed critical procedures, and exposed sensitive patient data. From unpatched software to unmonitored devices, these legacy technologies open the door to vulnerabilities that attackers are quick to exploit.
Here’s where the most common risks lie — and what healthcare organizations can do to reduce them.
The Critical Vulnerabilities Posed by Outdated Systems
Despite rapid innovation in medical technology, the healthcare industry still relies too much on legacy systems. As recently as 2021, 73% of hospitals were still using outdated software that was either unpatched or no longer compliant with modern security standards — needlessly increasing their exposure to well‑documented threats and making themselves easy targets for cybercriminals.
Outdated systems also present operational challenges, especially when it comes to interoperability, as older technologies struggle to reliably connect with newer systems — leading to inefficient data exchange and creating weak links that are harder to secure.
Further adding to this problem is the rapid proliferation of connected medical devices. More than 2 million Internet of Things (IoT) devices are currently in use across U.S. hospital systems, many of them communicating with legacy systems and expanding the threat surface. Many of these devices fly under the radar, with hospital IT teams completely unaware that certain devices are connected to the internet or haven’t been properly decommissioned when necessary. This combination of unmonitored connections and outdated infrastructure is a cyberattack waiting to happen.
4 Ways to Reduce Your Risk
Addressing the risk of outdated systems requires more than reactive fixes. It demands visibility, architectural safeguards, and active monitoring. Here are a few ways to mitigate your risk as you make long‑term plans to overhaul outdated infrastructure:
- Inventory All Internet‑Facing AssetsConduct a complete audit of all systems, devices, and applications exposed to the internet. This inventory is the first step in understanding where the vulnerabilities are.
- Implement Zero‑Trust ArchitectureA zero‑trust security model ensures that no system or user is automatically trusted, regardless of its location on the network. Every access request is verified, reducing the potential for a widespread breach.
- Centralize Device and Patch ManagementWithout centralized oversight, it’s nearly impossible to ensure consistent security. A single repository that tracks devices, software versions, and patch status helps teams stay on top of vulnerabilities and enforce uniform standards across the organization.
- Establish Enterprise‑Level Data Loss Prevention CapabilitiesCyber threats evolve quickly, so response mechanisms must keep pace. Data loss prevention systems provide real‑time alerts and allow for rapid mitigation when issues arise — minimizing downtime and protecting sensitive data.
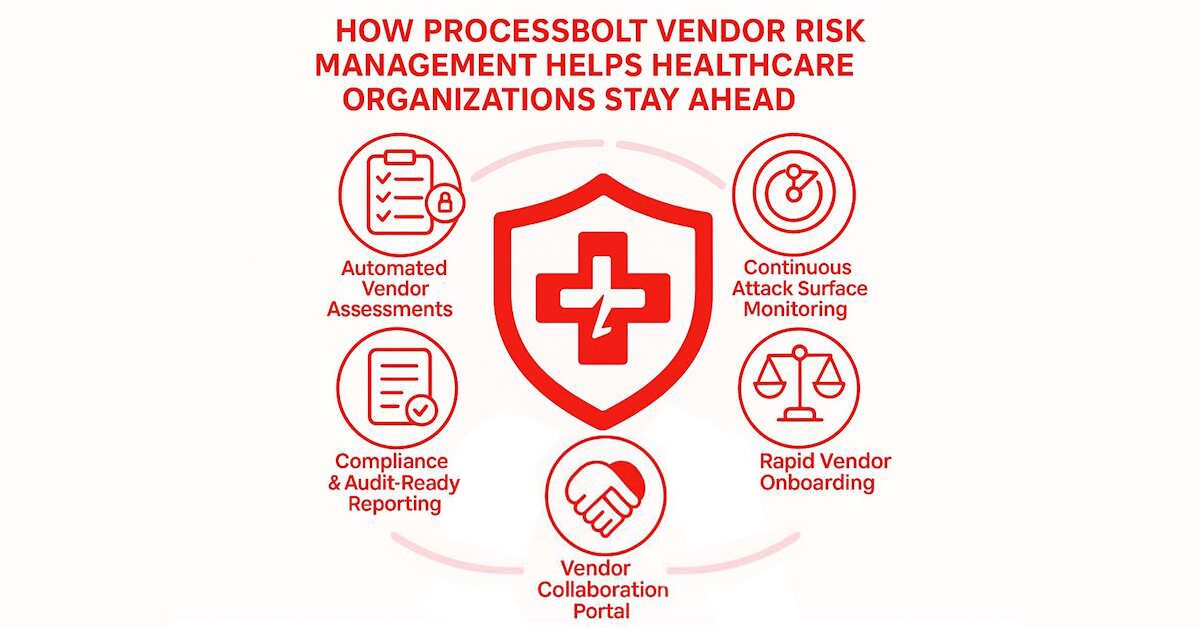
How ProcessBolt Helps Healthcare Organizations Stay Ahead
While most healthcare organizations know what they need to do, they lack the tools, time, and personnel to do it effectively and consistently.
That’s where ProcessBolt comes in.
ProcessBolt makes it easier to find and fix the vulnerabilities that arise from outdated healthcare systems. It gives IT and security teams a clear, centralized view of all devices and systems connected to the internet – whether internal or vendor‑managed. With this visibility, organizations can quickly identify what’s outdated, what needs patching, and what should be retired altogether. ProcessBolt also supports zero‑trust security principles by managing permissions and access across systems, and it helps automate continuous monitoring so problems don’t fall through the cracks between periodic reviews.
Finally, it’s simple and straightforward to use. Security programs tend to fall apart when they’re too complex to maintain, but ProcessBolt is designed to be easy to use so that hospitals can improve their security posture without overwhelming internal teams.
Closing the Gaps in Hospital Infrastructure
Outdated systems represent a growing liability in the healthcare industry. As cyber threats become more sophisticated and the number of connected devices continues to rise, unpatched software and legacy infrastructure expose hospitals to avoidable risk. But with the right approach — and the right tools – healthcare organizations can eliminate these vulnerabilities and build a more resilient cybersecurity strategy.
Proof in action: Within 90 days of deploying ProcessBolt, one 300‑bed Midwestern hospital cut its number of unpatched internet‑facing assets by 42 percent and reduced remediation time from weeks to hours.
Ready to see similar results?
Schedule a 15‑minute Risk Audit with a ProcessBolt security specialist and get a custom remediation roadmap for your hospital today.