Numerous surveys of the U.S. workforce and business owners indicate that return-to-office plans are still on hold, a fact that pleases a growing number of employees who have found increased productivity and reduced spending during the pandemic. However, business owners don’t share the same enthusiasm for one reason: External attack surfaces are growing at an alarming rate, faster than security teams can manage.
Everything outside a company’s firewall is discoverable by hackers, who comb the internet searching for vulnerable organizations. As the threat landscape expands, authorities, such as Gartner, now recommend that security leaders monitor and manage their attack surfaces as part of their overall cybersecurity risk management programs.
In Gartner’s Security Operations Primer for 2022, they advise security and risk management leaders to:
- Use automation to augment and accelerate processes and activities
- Gain a better understanding of the expanding attack surface
- Embrace as-a-service security capabilities.
Attack surface management must now be a top priority for CISOs, CTOs, CIOs, and security teams due to decentralized work environments. But this relatively new term, and the steps to incorporate it into a risk management program, can confuse some.
What is ASM?
Attack surface management (ASM) is the continuous discovery and monitoring of internet-facing assets—websites, applications, and IP addresses—that are vulnerable to a cybersecurity breach. These assets can easily transmit sensitive data, luring hackers.
When you think of your own organization, think about all the hardware, software, cloud apps, SaaS products, vendors, and more that require you to do business daily. Each one of these attack surfaces, especially those outside the firewall or endpoint protection services, must be watched and monitored.
These can include:
- Known assets such as your corporate website and servers
- Unknown assets such as a forgotten website or app, or a marketing landing page
- Unauthorized assets such as a website created by a threat actor to impersonate your domain
- Vendors, including third- and fourth-party, who can introduce cyber risk, leading to wide-scale data breaches
ASM can sound like a tall order, but with the right monitoring software, attack surface management runs on autopilot, alerting you to a potential weakness in your security or an impending breach before it occurs.
Why Choose ThreatScape?
ProcessBolt’s proprietary attack surface management tool, ThreatScape, helps keep you ahead of an attack by continuously monitoring all attack surfaces and providing a hacker’s view of the gaps in your environment. ThreatScape takes your organization beyond pentesting and vulnerability scanning to close these gaps.
To use, simply load one or more domains into ThreatScape and the tool automatically monitors all associated attack surfaces on a 24/7 basis.
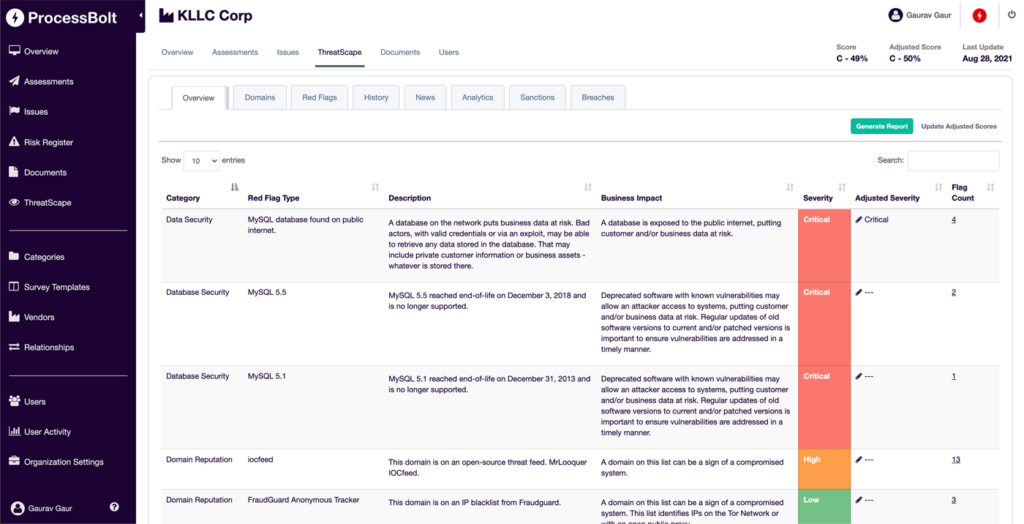
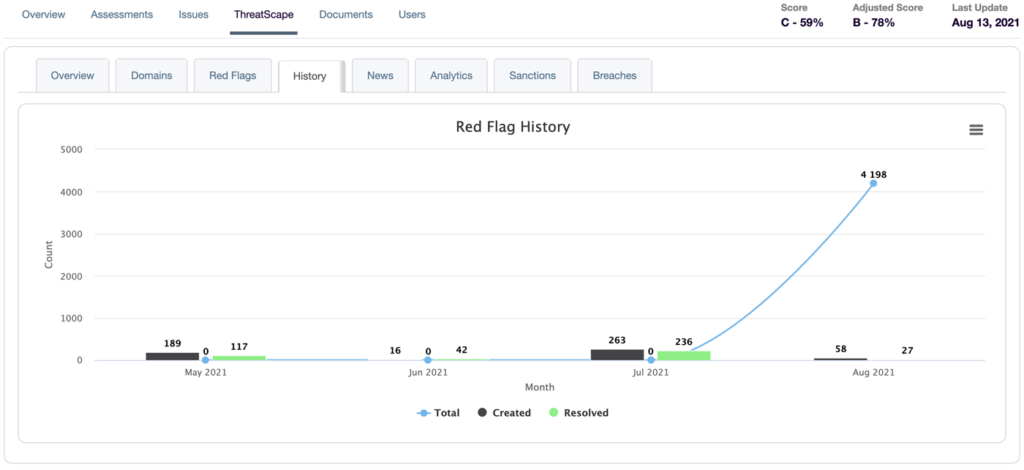
A real-time dashboard alerts you to any red flags by identifying unauthorized activity, allowing you to remediate potential threats before they occur. For vendors, ThreatScape can identify risks that may affect risk assessment ratings and remediation recommendations.
Try ThreatScape Free for 30 days
Complete the below form for a demo of the ProcessBolt platform, which includes a customized walkthrough of ThreatScape, and you’ll receive a one-month, fully functioning subscription to ThreatScape. Load your domains into the platform and watch as ThreatScape alerts you to potential vulnerabilities you never knew you had.




