Detect Exposure
Mitigate Risk
With ProcessBolt’s Continuous Vendor Risk Management Platform
Gain visibility into vendor-based threats with our collaborative,
user-friendly and automated solution.
We Protect the World’s Top Brands

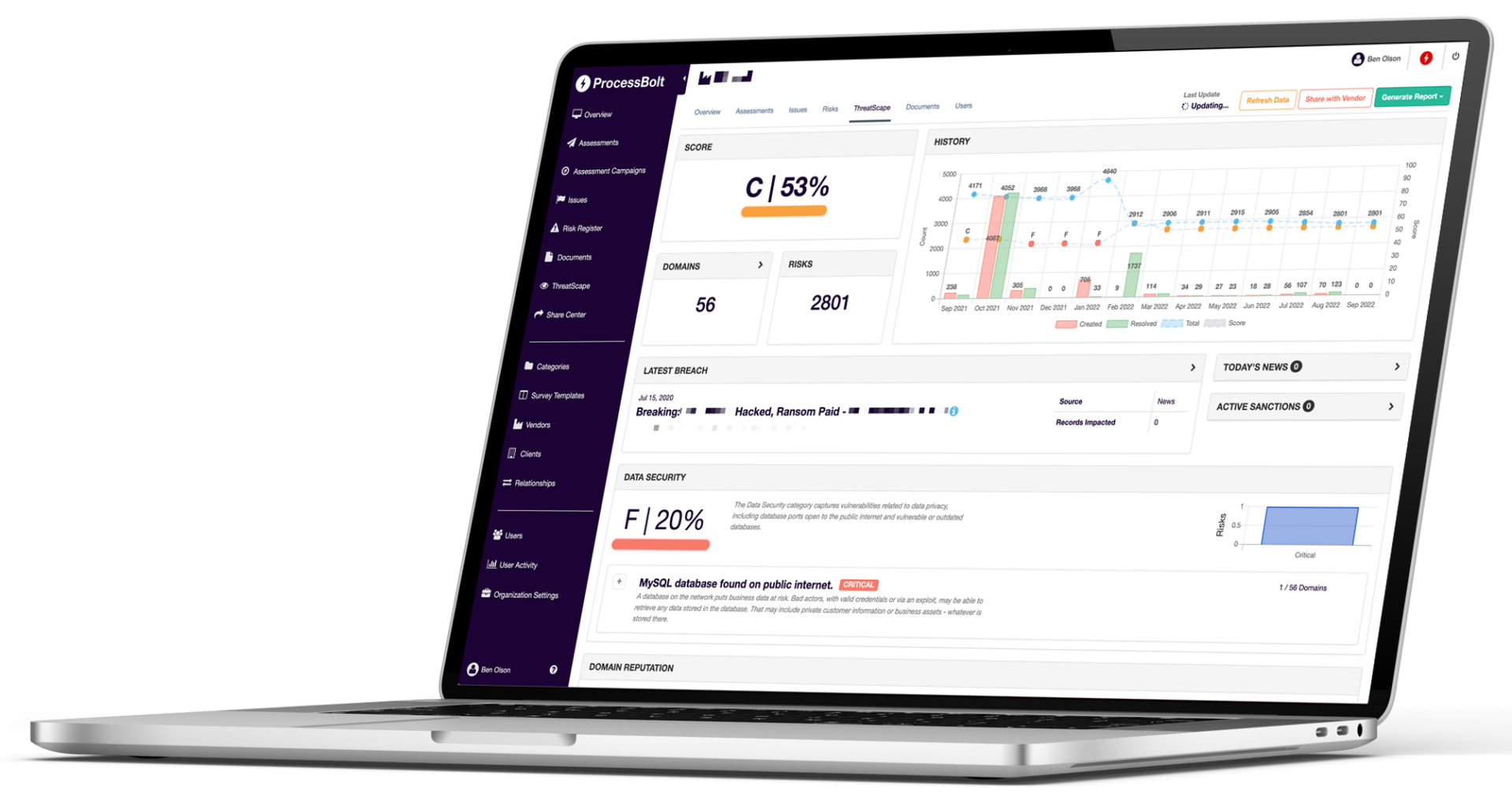
See a 360 view of your security posture 24/7
Secure your supply chain with a single employee with ProcessBolt’s unified platform and automation tools. Correlate and verify your vendors’ risk attestations with real-time attack surface data to ensure your vendor network always remains secure.
Assess + Monitor + Extract + Correlate = VERIFICATION

Automate
Automate Risk Assessments
- Automate, streamline and collect vendor assessments with effortless onboarding in minutes
- Pre-configured and customizable assessment templates covering every major regulatory structure
Monitor
Continuously Monitor
- Continuously monitor each vendor’s attack surface data and receive real-time alerts using our own sourced data to minimize false positives.

Extract
Extract Intelligence
- Use AI to analyze vendor policy documents and reduce vendor response times by 80%.

Verify
Verify Security
- Correlation of assessment data, attack surface data and intelligence from policy documents provides an exceptionally high level of verification of the security posture of your supply chain
FEATURES & BENFITS
Unified Platform
Assessments, attack surface data and risk policy documents are correlated to verify your supply chain network
Proprietary
Tools and data are built in-house. Most competing solutions buy their data, meaning they have no control over timeliness or accuracy and alerts are not real-time
Resource Focused
A single person can manage the entire vendor risk management process with the ability to communicate and delegate between vendors or teammates as needed
Trust But Continuously Verify
Expert derived correlations continuously ensure vendors are doing what they say 24/7
Trust & Security
Your data remains securely within our environment, fully under your control, and is never used for training large language models
No Hidden Fees
One price – no hidden service or user fees
Customizable
Customize workflows, assessments and risk tolerance to fit your organizations needs and provide a unique program for each customer
Zero Hallucination
If our DocAI tool is less than 99% certain about an answer, it won’t provide one to protect you from incorrect responses or misleading information being sent to a vendor
Compliance Ready
Customized workflows for NIST, SIG, ISO, HIPAA, CCPA, GDPR, CMMC, SOX, DORA and more
Best in Class Risk Management Solution
ProcessBolt’s best-in-class platform
provides instant verification and continuous security
%
SECURITY BREACHES ARE RELATED TO THIRD PARTIES
AVERAGE COST OF A SECURITY BREACH
%
EXPECTED INCREASE IN THIRD PARTY RELATED INTRUSIONS
See ProcessBolt’s best-in-class VRM process yourself
Sign up to speak to a security expert and receive a personalized demo to see what ProcessBolt can do for you.
What Users Say
"Customer Experience is Great!"
The Processbolt team has been incredibly receptive to feedback and requests for help. Processbolt has been essential to us being able to track and be able to complete security assessments."Best Vendor Management Tool!"
ProcessBolt was very fast for our team to implement and start using. They also have an unlimited user model, which works in our favor, and the platform is straightforward to use."Win with ProcessBolt"
ProcessBolt makes it easy to automate our vendor management process. The team is really helpful and truly care about us getting value out of the system, which we do."GREAT ASSESSMENT PLATFORM"
ProcessBolt is an extremely easy-to-use and flexible assessment platform. The tool is agnostic to any one methodology. It can be customized to your company’s specific rule sets to measure vendor’s risk or leverage one of ProcessBolt’s templates. Their support team is super helpful if you want to get more detailed, and the team is always willing to help walk you through something.ProcessBolt News
Why Manual Third-Party Risk Management No Longer Works
Manual third-party risk management processes waste resources and create blind spots. Learn how automation and AI can secure your third-party ecosystem.
Vendor Risk Automation in 10 Days or Less with ProcessBolt
Learn how ProcessBolt delivers vendor risk automation in 10 days or less with no-code tools, prebuilt templates, and hands-on onboarding support.
How Tariffs Impact Manufacturing Security
Tariffs reshape manufacturing security by driving supplier shifts, workforce cuts, and documentation risk. Learn how to adapt your cybersecurity and TPRM strategies.