Gain Visibility Into Your Third-Party Based Threats
Safeguard Your Firm
with Automated Third-Party Risk Management
Confidently Secure Your Law Firm From Third-Party Breaches.
ProcessBolt streamlines risk assessments and integrates continuous attack surface monitoring, giving you real-time insights into your vendors’ security—protecting your firm from potential threats.
Cyber Threats
from Third-Party Attacks
Law firms face severe financial and reputational damage from data breaches, including legal penalties and lost clients. To avoid these risks, they must enforce strong security measures like multi-factor authentication and continuous monitoring of third-party vendors. Regular risk assessments and effective vendor management are essential to identifying vulnerabilities and protecting sensitive data.
$2M
Brand Damage & Lost Business
$5M
Average Ransomware Demand
$10M
Average Class Action Settlements
See a 360 view
of your security posture 24/7
Ensure your vendor network stays secure and compliant effortlessly by automating vendor risk assessments and continuously monitoring attack surface data in real-time. Enjoy peace of mind as your risk management process runs smoothly and successfully, without the stress of manual oversight.
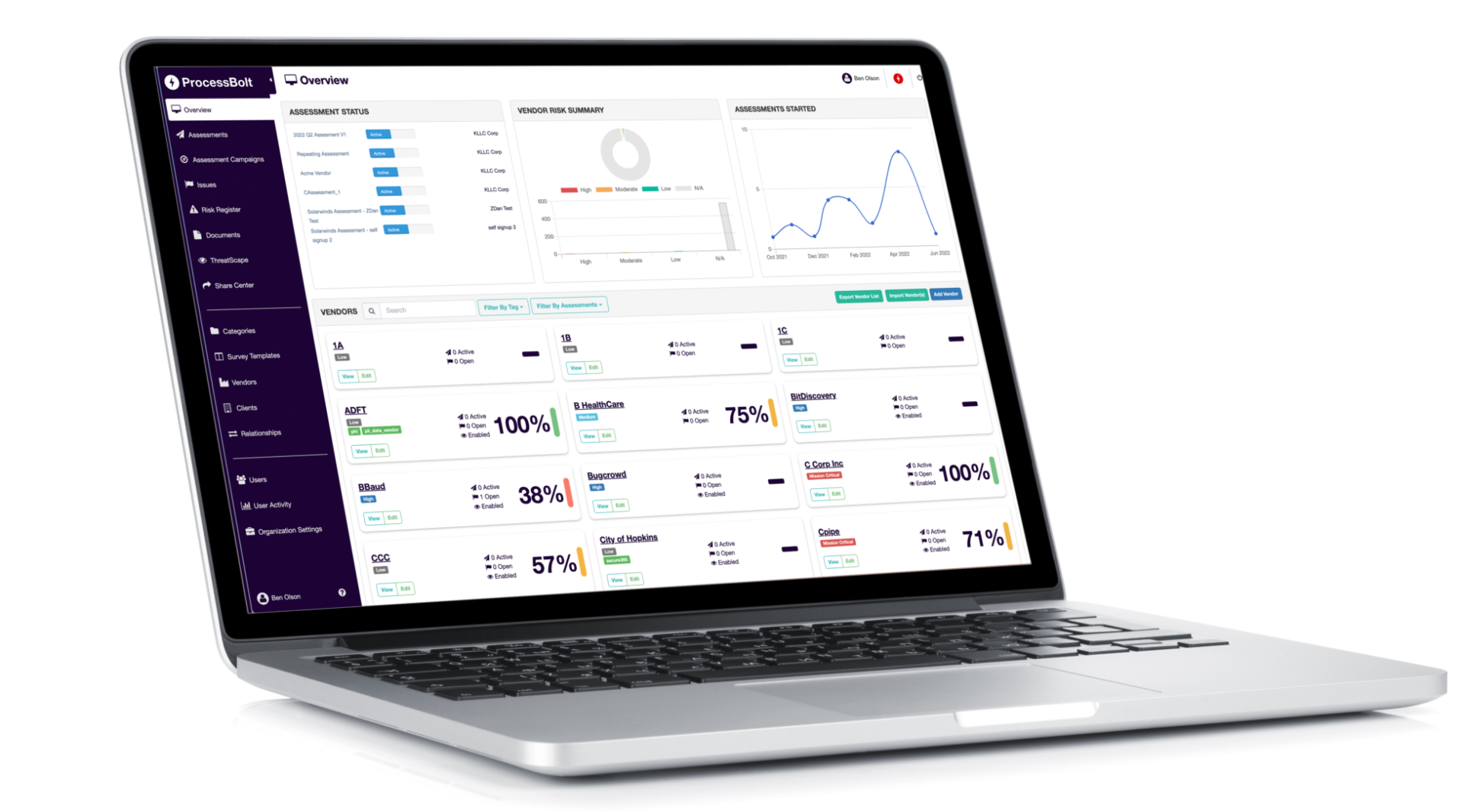
VENDOR RISK ASSESSMENTS
ProcessBolt is a fully integrated platform that automates the extraction of intelligence directly from vendor policy documents to populate security assessments. It correlates this data with the vendor’s attack surface intelligence, drastically reducing assessment timelines from weeks to minutes.
FULLY AUTOMATED ASSESSMENT PROCESS
Purpose-built, automated workflows help you eliminate spreadsheet management while improving accuracy
ADAPTABLE
Build a custom assessment or leverage our robust library of templated questionnaires such as NIST, ISO, SIG, ESG, DORA, GDPR, and HIPAA
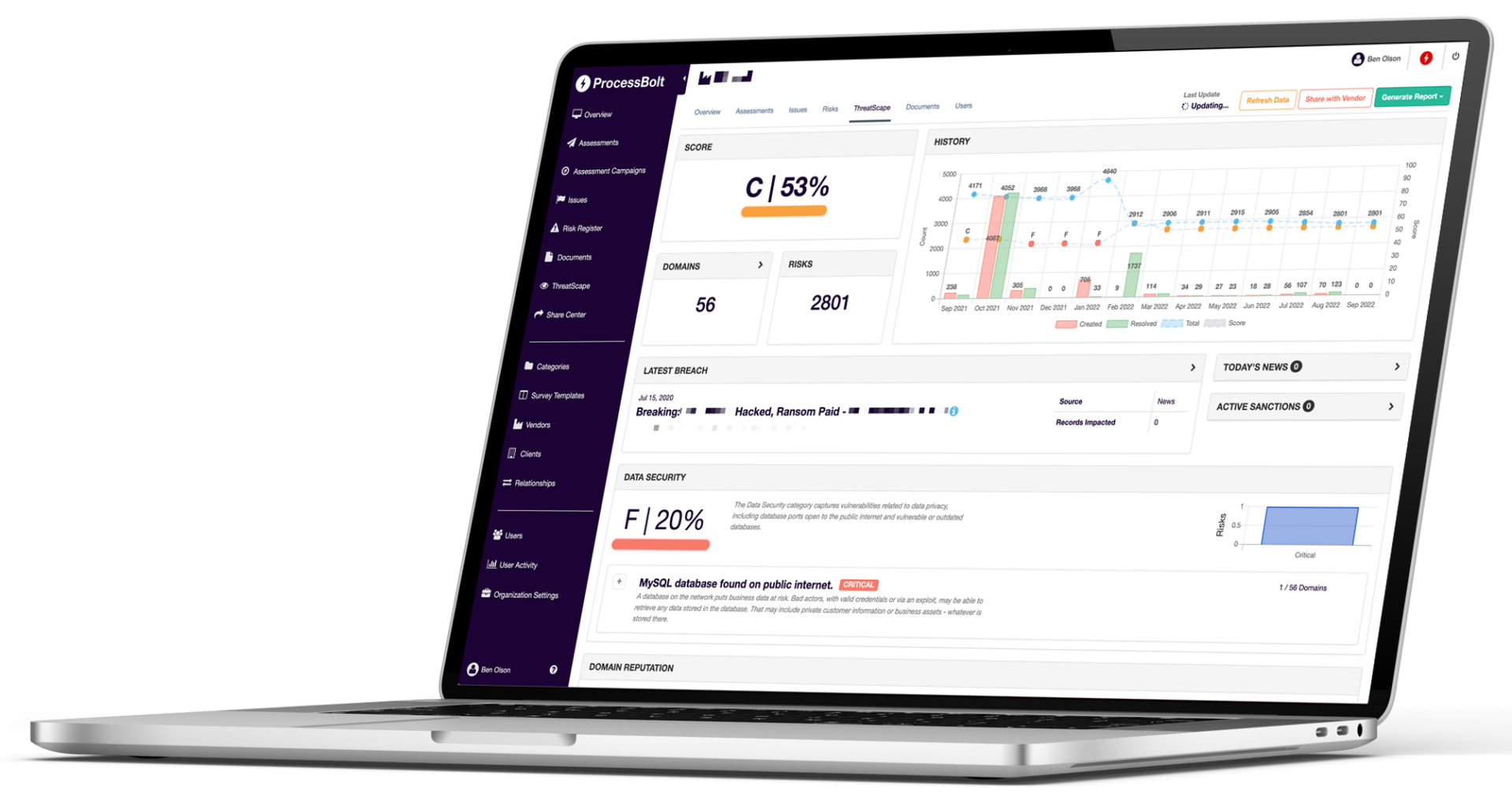
CONTINUOUSLY MONITORING
ThreatScape Attack Surface Management platform protects against gaps in your company’s and your vendors’ digital ecosystem by identifying and monitoring internet-facing assets in real-time.
ENTERPRISE BENEFITS
Identify risks that may not be uncovered in the vendor risk assessment process or risks that surface in between assessments
REAL-TIME ALERTS
Monitor your enterprise, and your vendors, and receive alerts in real-time regarding adverse changes in security posture and actionable intelligence to remediate the issues
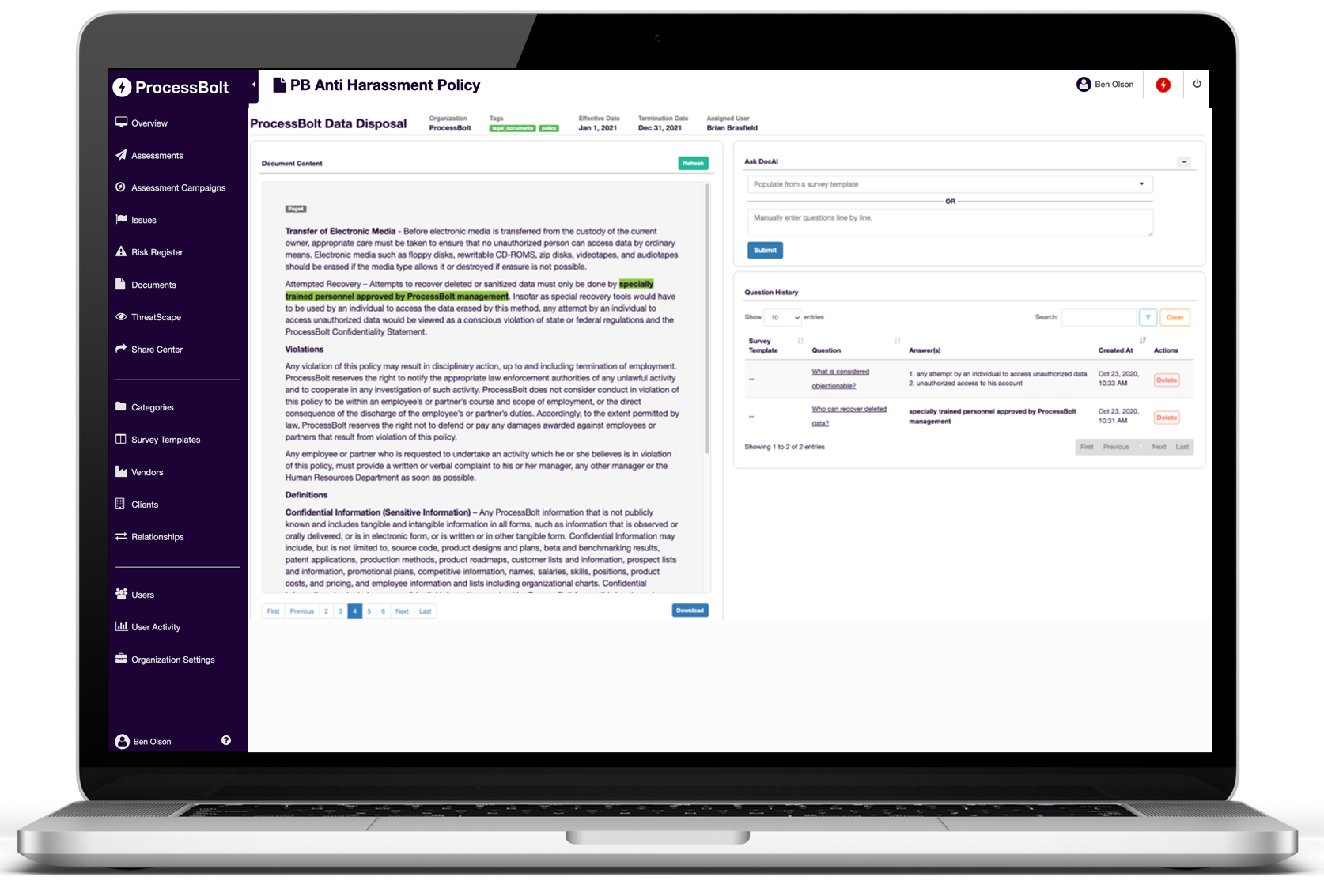
EXTRACT INTELLIGENCE
DocAI eliminates the need to read the full text, by using deep natural language processing to extract intelligence from vendor evidentiary documentation as part of the assessment process. Our patent pending technology allows teams to focus on the results instead of spending time reading through countless documents.
AI SUPPORTED QUESTIONS AND ANSWERS
Ask any English language question to a single document or a series of documents, and DocAI answers the question and highlights where the answer was found
DOCUMENT SUMMARIZATION
DocAI uses natural language processing and machine learning to understand the content and structure of a document, and then generates a summary that captures the essence of the original text
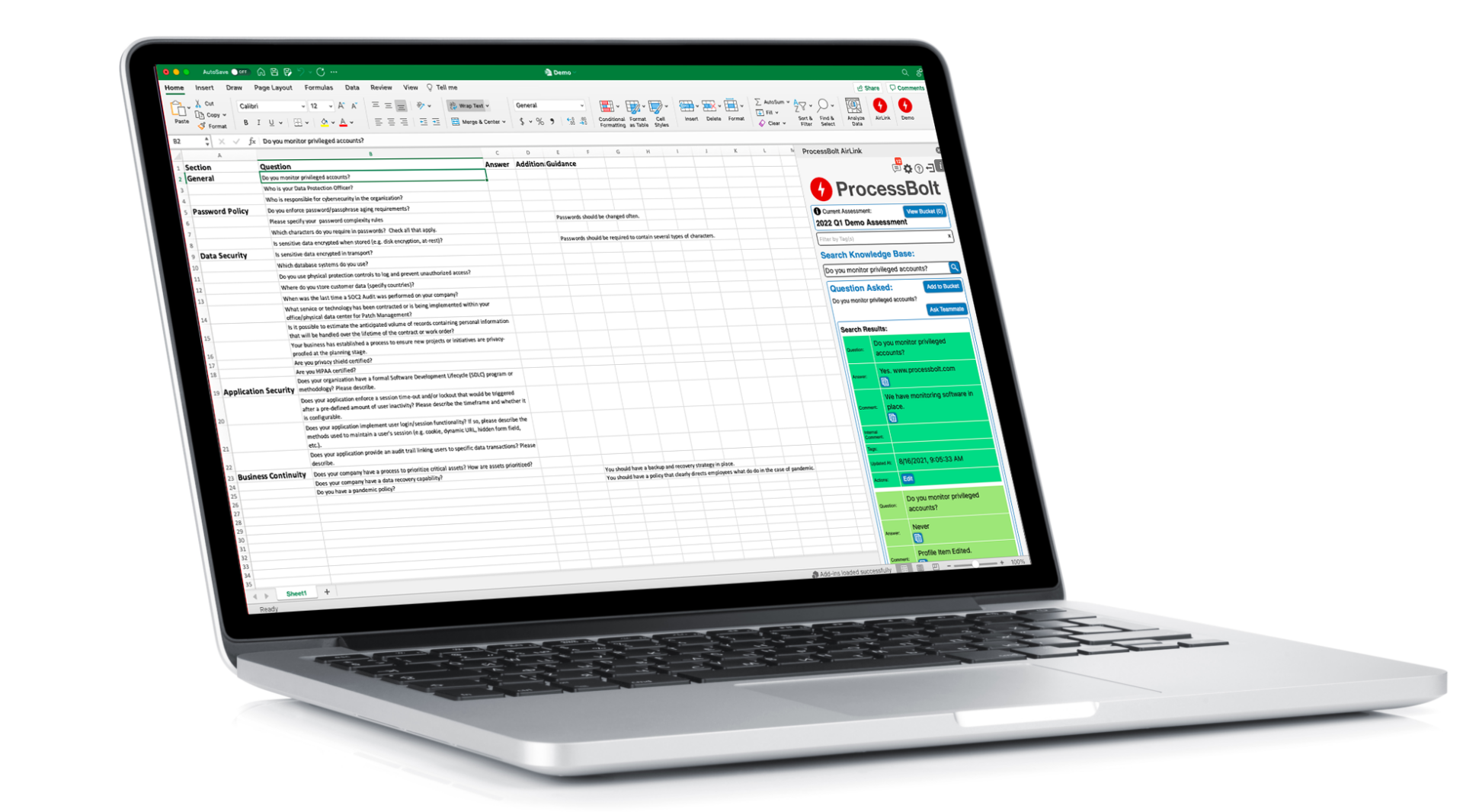
VENDOR ASSESSMENT RESPONSE SOLUTION
AUTO-RESPONSE
Proprietry AI technology allows you to quickly auto populate assessments and RFPs from previous responses, ensuring consistency and alleviating redundant work
SHARE CENTER PRE-EMPTIVE INFORMATION SHARING
Includes a data warehouse, which enables sharing of key documents at any time with customers

Trusted by Leading Law Firms
for Third-Party Risk Management
ProcessBolt supports top AMLAW 200 and NLJ500 law firms by delivering automated third-party risk management solutions that streamline assessments, monitor vendors in real-time, and ensure regulatory compliance, helping top firms safeguard sensitive data and reduce risks efficiently.






ProcessBolt’s best-in-class platform
provides instant verification and continuous security
%
SECURITY BREACHES ARE RELATED TO THIRD PARTIES
AVERAGE COST OF A SECURITY BREACH
%
EXPECTED INCREASE IN THIRD PARTY RELATED INTRUSIONS
See ProcessBolt’s best-in-class VRM process yourself
Sign up to speak to a security expert and receive a personalized demo to see what ProcessBolt can do for you.
FEATURES & BENFITS
Unified Platform
Assessments, attack surface data and risk policy documents are correlated to verify your supply chain network
Proprietary
Tools and data are built in-house. Most competing solutions buy their data, meaning they have no control over timeliness or accuracy and alerts are not real-time
Resource Focused
A single person can manage the entire vendor risk management process with the ability to communicate and delegate between vendors or teammates as needed
Trust But Continuously Verify
Expert derived correlations continuously ensure vendors are doing what they say 24/7
Trust & Security
Your data remains securely within our environment, fully under your control, and is never used for training large language models
No Hidden Fees
One price – no hidden service or user fees
Customizable
Customize workflows, assessments and risk tolerance to fit your organizations needs and provide a unique program for each customer
Zero Hallucination
If our DocAI tool is less than 99% certain about an answer, it won’t provide one to protect you from incorrect responses or misleading information being sent to a vendor
Compliance Ready
Customized workflows for NIST, SIG, ISO, HIPAA, CCPA, GDPR, CMMC, SOX, DORA and more



